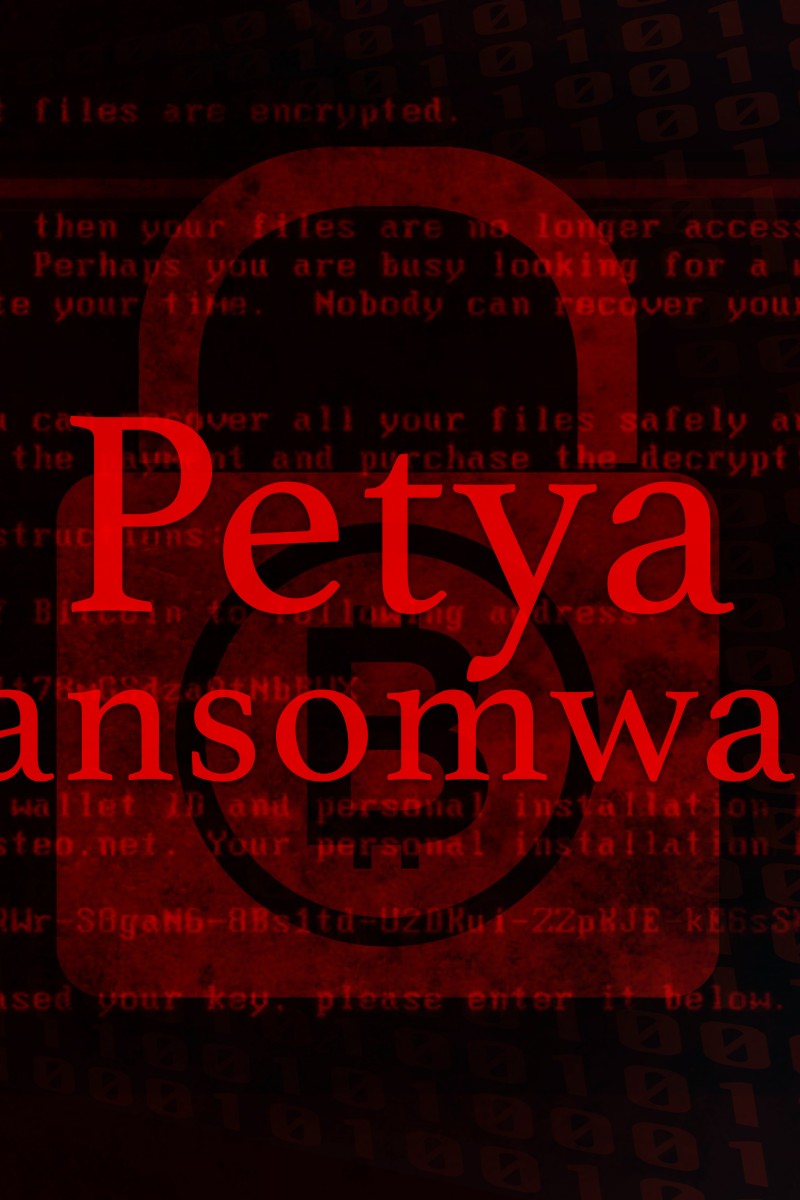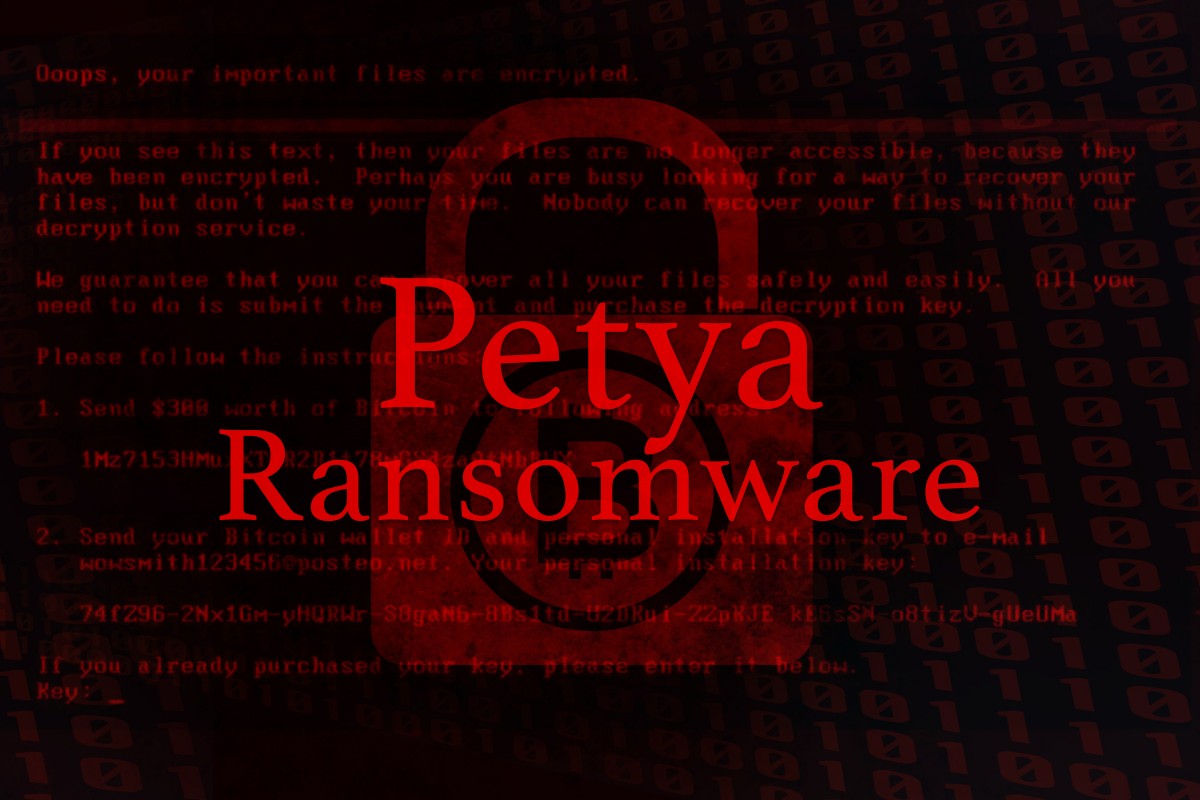
Many organisations in Europe and the US have been crippled by a ransomware attack called “Petya”. The awful software has spread through large companies, leading to PCs and data being locked up and held for ransom.
Petya is the second major global ransomware attack in the last two months. In early ransomware WannaCry took control of 230,000 computers in over 150 countries, demanding money to release them. Like WannaCry, Petya spreads rapidly through networks that use Microsoft Windows, but what is it, why is it happening and how can it be stopped?
What is ransomware?
Ransomware is a type of malware that blocks access to a computer or its data and demands money to release it.
How does it work?
When a computer is infected, the ransomware locks down important documents and files and then demands money, typically in Bitcoin, for a digital key needed to unlock the files. If victims don’t have a recent back-up of the files they must either pay the ransom or face losing all of their files.
What should you do if you are affected by the ransomware?
Petya infects computers and then waits for about an hour before rebooting the machine. While the machine is rebooting, you can switch the computer off to prevent the files from being locked down. Then you can try to rescue the files from the machine, as flagged by @HackerFantastic on Twitter.
If the system reboots with the ransom note, don’t pay the ransom – the “customer service” email address has been shut down so there’s no way to get the decryption key to unlock your files anyway. Disconnect your PC from the internet, reformat the hard drive and reinstall your files from a backup.
Back up your files regularly and keep your anti-virus software up to date!
How does the Petya ransomware work?
The Petya ransomware takes over computers and demands US$300, paid in Bitcoin. It spreads quickly across an organisation once a computer is infected using the EternalBlue weakness in Microsoft Windows. Microsoft has released a patch, but not everyone will have installed it. It it can't get through Eternal Blue, Petya will use two Windows administrative tools. It tries one option and if it doesn’t work, it tries the next one.
Where did it start?
The attack seems to have been seeded through a software update mechanism built into an accounting program that companies working with the Ukrainian government need to use, say the Ukrainian Cyber Police . This explains why so many Ukrainian organizations were affected, including government, banks, state power utilities and Kiev’s airport and metro system. The radiation monitoring system at Chernobyl was also taken offline, forcing employees to use hand-held counters to measure levels at the former nuclear plant’s exclusion zone.
How far has it spread?
Petya has caused serious disruption at large firms in Europe and the US, including the advertising firm WPP, French construction materials company Saint-Gobain and Russian steel and oil firms Evraz and Rosneft. The food company Mondelez, legal firm DLA Piper, Danish shipping and transport firm AP Moller-Maersk and Heritage Valley Health System , which runs hospitals and care facilities in Pittsburgh, also said their systems had been hit by the malware.
So is this just another opportunistic cybercriminal?
At first it looked like Petya was just another cybercriminal taking advantage of cyberweapons leaked online. However, security experts say that the payment mechanism of the attack seems too amateurish to have been carried out by serious criminals.
Firstly, the ransom note includes the same Bitcoin payment address for every victim – most ransomware makes a custom address for every victim.
Secondly, Petya asks victims to communicate with the attackers via a single email address which has been suspended by the email provider after they discovered what it was being used for. This means that even if someone pays the ransom, they have no way to communicate with the attacker to request the decryption key to unlock their files.
OK, so then who is behind the attack?
It’s not clear, but it seems likely it is someone who wants the malware to seem to be ransomware, while actually just being destructive, particularly to the Ukrainian government. Security researcher Nicholas Weaver told cybersecurity blog Krebs on Security that Petya was a “deliberate, malicious, destructive attack or perhaps a test disguised as ransomware”.
Ukraine has blamed Russia for previous cyber-attacks, including one on its power grid at the end of 2015 that left part of western Ukraine temporarily without electricity. Russia has denied carrying out cyber-attacks on Ukraine.